CISO Radar 2024: Adaptation, Collaboration, and Transformation in Cybersecurity
Published May 16, 2024
- Cybersecurity

Cybersecurity in 2024: what to expect?
Before long, the Olympic flame will be lit, and the Paris Games will be launched. This global event will attract a great deal of attention, including when it comes to cyberattacks! Cybersecurity teams will obviously need to pay close attention, to prevent possible incidents during the competition… without overlooking their day-to-day programs, and major transformation projects in anticipation of new threats, regulations, and technologies.
Prepare your 2024 (and beyond) strategy by exploring with us the major trends that will transform the cybersecurity landscape this year.
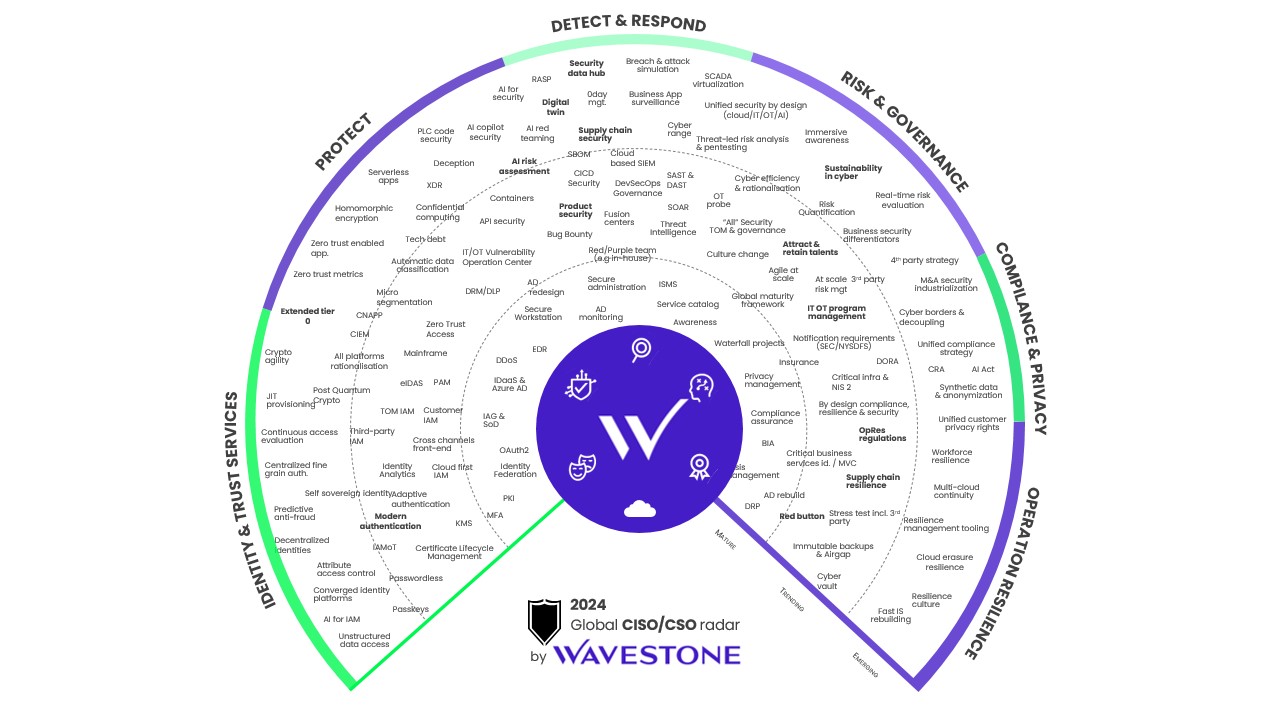
The 2024 global CISO/CSO Radar by Wavestone
For the past 10 years, Wavestone has been annually updating its forecasting tool, the “CISO Radar”, which brings together all the key issues for the cybersecurity and operational resilience fields. It highlights our latest engagements and the changes observed by all our cybersecurity and operational resilience experts.
Based on this radar and our analyses, we have identified the 10 most important shifts for the 2024-2027 era.
Matching cybersecurity basics to future challenges
1. Cloud: two challenges for cyber teams
To securely harness the Cloud’s full potential, your first challenge is to break down silos. Many organizations have isolated this technology, by creating centers of excellence or appointing dedicated experts, without integrating them within existing security or IT teams. Although this was necessary to get the technology off the ground, it is now having a detrimental effect. Faced with the increase in Cloud-native or hybrid projects, operational changes are needed to take the burden off Cloud security teams. The Cloud must become an IT system like any other. Cloud security also needs to be onboarded into the CI/CD chains and agile methodologies deployed in organizations, including for internal systems.
Your second challenge: Cloud opportunities in terms of cybersecurity are still under-exploited. These include:
- Automated deployment of resources and security policies.
- Visibility into the Cloud environment, enabling better perimeter monitoring.
- Development of new resources, with no code / low code (no need to code to deploy) or no admin (fewer users with administrator roles) strategies.
This can often be explained by insufficient team training, or by the large number of features offered by Cloud services, and their rapid development pace. Analyzing the existing capabilities of Cloud platforms and aligning them with the organization’s cyber processes is often a very positive step and enables you to deal with issues that have been outstanding for years (real-time compliance checks, security policy monitoring, etc.).
Extended Tier 0 in Cloud deployment
Extended Tier 0 can be understood as an extension of the Tier 0 concept to the Cloud, i.e. the area hosting systems providing broad, in-depth access to the IS. In the Cloud, we are looking at secure management of high-privilege accounts, by linking traditional security principles with features and functions specific to Cloud environments.
This extended version is designed to provide:
- Extended access to resources. Extended Tier 0 accounts expand privileges beyond an individual system or a specific domain, protecting access to multi-platform or multi-service elements.
- Centralized privilege management. Extended Tier 0 becomes the central access and privilege control point for different cloud environments.
- Security and compliance. Because of their level of privilege, superadministrator accounts must be the most secure and follow strict compliance with security policies, regardless of their location or the underlying technology.
2. Zero Trust: towards a global strategy
Zero Trust is a target for almost all our clients. Several assessment frameworks are available today (including Wavestone’s) for drawing up a transition plan towards a Zero Trust model that is effective on several dimensions: infrastructure, applications, access etc.
Large organizations are currently carrying out two types of projects.
- ZTNA (Zero Trust Network Access) deployment, which focuses on network and remote access.
- Micro-segmentation, which involves dividing the network into segments and dynamically applying specific security policies to them.
But Zero Trust is not limited to remote access and micro-segmentation. The greatest challenge is to gradually migrate applications to a Zero Trust model. This is a profound and complex change that takes time. Mature organizations are currently building a convergent approach where adoption progress is measured incrementally through tangible metrics. These include: the percentage of critical applications managed with conditional access, coverage of users by Zero Trust access, coverage of critical environments by micro-segmentation and the number and precision of criteria for assessing the level of trust.
It’s a progressive yet steady movement, which needs to be driven and sustained over time.
Modern Authentication: what’s behind the buzzword?
You may have come across these words a few times, albeit with different interpretations. Broadly speaking, Modern Authentication is a combination of best practices in identity and access management. It is based on:
- implementation of recent authentication and authorization protocols, such as OIDC (Open ID Connect), OAuth 2.0 (Open Authorization 2.0) and SAML (Security Assertion Markup Language);
- multiple authentication factors, via passkeys, tokens, certificates or even passwords, although passwordless methods are preferred;
- deployment of a conditional access strategy.
To sum up, Modern Authentication brings together measures that are already being deployed, but which still have a long way to go before they are mature. Improving authentication and authorization techniques remains a key concern for many of our clients.
3. Culture change: new ways to raise awareness of cyber risks
Awareness-raising is one of the most widespread practices in cybersecurity and has been for years. However, phishing campaigns often deliver disappointing results, pointing to a “glass ceiling” being reached, and highlighting the urgent need to rethink cybersecurity training and bring it closer to the field, to the highest-risk areas.
The aim is not to break through this ceiling, which would require an excessive amount of energy, but rather to specialize awareness campaigns to successfully change behavior.
The four actions below prove to be the most effective.
- Identify major risk areas related to business operations.
- Work closely with business units and employees to review and improve processes. It’s no longer a question of spreading broad, generic messages, but rather of looking at how to change ways of working with those who actually carry them out.
- Be creative, but always pragmatic, when adapting security practices.
- Measure the impact of your changes.
The TAMAM framework: a tool for raising cybersecurity awareness
The TAMAM method, developed by our team, aims to raise your employees’ awareness in a different way. Through positive, concrete and varied actions, we are convinced that an awareness-raising program must generate commitment while respecting the teams’ business context.
More specifically, it involves setting up a program aimed both at changing behavior and developing a safety culture within your organization. It is based on 5 pillars:
- Target – Set concrete, measurable objectives
- Audience – Tailor your approach to your target audience
- Message – Choose a short, optimistic message that calls for action
- Actions – Implement effective, practical and varied actions
- Measure – Evaluate the program’s impact on behavior
TAMAM offers a methodological renewal of awareness-raising, to give it new meaning and achieve better results.
4. Decoupling: no more globalized IS
Geopolitical turmoil over the past few years and stricter regional regulations suggest that a fully onboarded international IS is no longer an option. Some international organizations are already segmenting their IS into more localized versions, around two or three major zones. This trend is gaining momentum.
This new landscape offers two ways forward for organizations.
The proactive approach aims to restructure your architecture over the long term to create between two and four different zones.
- Build a segmented AD (Active Directory) (e.g., ensure the localization of domain controllers).
- Add a layer of security to foreign subsidiaries or entities (e.g., set up firewalls and filtering rules).
- Maintain a global detection capability by consolidating alerts rather than just logs.
- Ensure that third-party contracts are assessed from a sovereign geopolitical standpoint (e.g., hire local players able to deploy on-site in case of incident).
The reactive approach focuses on setting up crisis mode when rapid decoupling is required.
- Identify sensitive geographical areas.
- Implement Red Button procedures to shut down the network, privilege accounts, and access to applications and workstations.
- Anticipate business impacts and legal risks of isolation (e.g., when transferring security systems from an embargoed country).
Decoupling calls for a radical change in IS management and, in the future, cybersecurity. It requires cross-functional discussions with, on the one hand, top management, who are involved in the same way as in M&A operations, and, on the other hand, business units, to fully understand access and communication needs at company scale. Multinationals often have a dual objective when it comes to unbundling: to keep their business running as smoothly as possible and, at the same time, to protect themselves against espionage, malicious acts or attacks.
It is vital to find this new balance before being compelled to react in a state of emergency.
Digital twins – a key to decoupling
Digital twins are virtual, real-time representations of objects, systems or even more complex entities, such as the international network or a datacenter. Widely used in the industrial sector, they are beginning to spread amongst IT Departments.
From a cybersecurity point of view, they are useful for:
- Understanding the infrastructure/product and assessing changes impact through a virtual model.
- Conducting tests on a partitioned environment, whether for simulating attacks or deploying a security measure. These enable you to measure results and assess the effects of possible attacks.
- Vulnerability management and anomaly detection by modeling normal behavior.
Digital twins are still an emerging topic but could become increasingly important as more technologies can be used.
Working with new partners to strengthen security
5. Resilience: a key challenge
Operational resilience has become an absolute must in recent years, with new regulations such as DORA (Digital Operational Resilience Act) for the financial sector, NIS2 (Network and Information Systems Directive) and the future CRA (Cyber Resilience Act). Despite growing investment, the degree of maturity in this area remains low, with significant disparities between organizations.
How resilient are organizations?
Our 2023 Cyber Benchmark shows that :
- 31% of large organizations have mapped their critical value chain.
- 44% regularly test data recovery.
- 51% perform crisis exercises.
Operational resilience is complex, with wide disparities between the most resilient organizations (> 60%) and the least mature (30%). Half of the organizations included in the Cyber Benchmark 2023 have a maturity level below 50%.
The new European NIS2 directive, adopted on November 10, 2022, should have a positive impact on the resilience maturity of organizations, large and small.
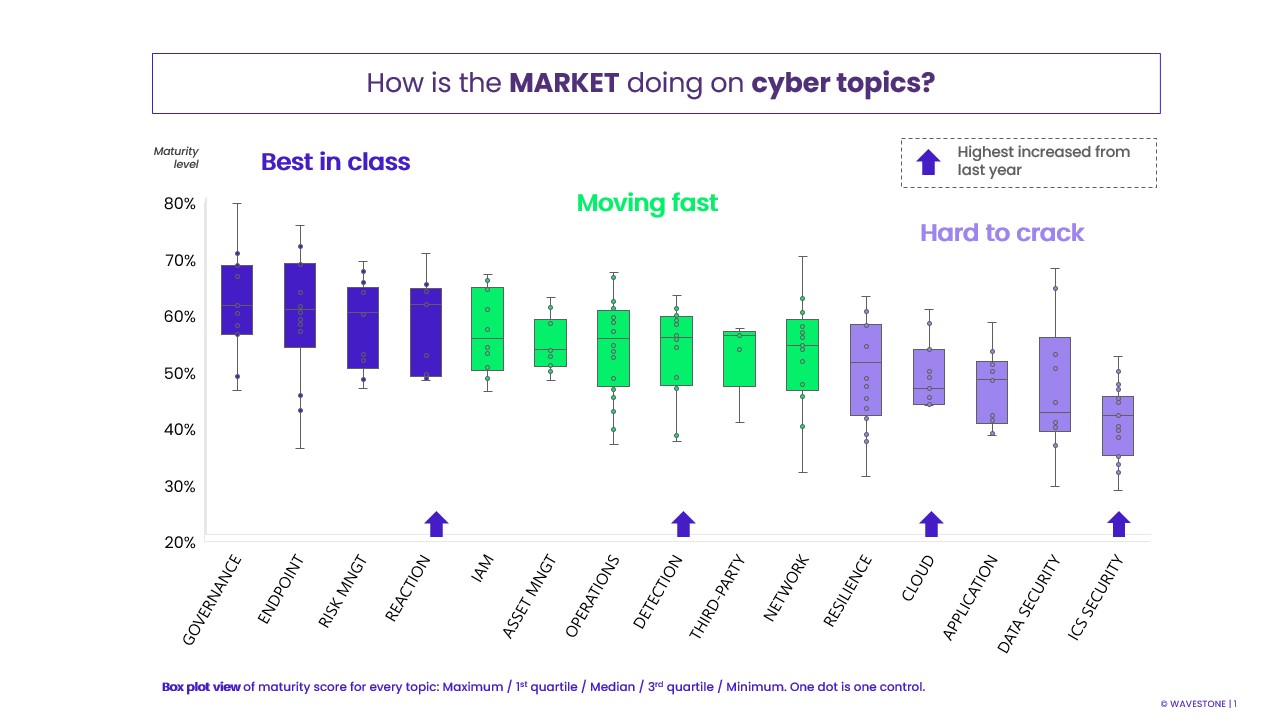
How is doing the market on cyber topics?
Resilience’s main objective is to protect your core business, your “Minimum Viable Company”. This means asking the right questions and working with the right people.
In a top-down approach, you work together to:
- Identify critical value chains, whose disruption would have the greatest impact on your organization (e.g., cash flow unavailability, inability to place orders, etc.).
- Assess your risk tolerance and define acceptable limits, or “red zones”, beyond which you can’t go (in other words, agree on the “worst acceptable”).
This approach is not limited to cybersecurity but encompasses a broader set of risks to be covered – including security and safety.
Involving operational staff in resilience programs is essential to accurately map critical resources, in line with the organization’s activity. This enables you to:
- List tools, procedures, users, administrators, third parties, etc.
- Formalize risk scenarios, including those that could lead to “red zones”.
Our field experience shows that, of all risk scenarios faced by an organization, ransomware is (not surprisingly) one of the most frequent.
This risk is often addressed using the ARM (Avoid, Recover, Maintain) method. It summarizes the three main objectives that guarantee resilience.
- Avoid, i.e., implement a strategy to prevent risks, in particular by assessing the ability to detect the main stages of the killchain based on MITRE ATT&CK analysis.
- Recover, i.e., reduce reconstruction time should the critical chain be destroyed.
- Maintain, i.e., ensure operational continuity during a crisis.
Operational resilience is a long-term process, involving a large number of people in the organization. Required effort should not be underestimated. However, it does deliver tangible results when problems arise!
6. Third-party management: a cooperative effort
Third-party attacks increased in 2023. The latest attacks on Boeing, ICBC and DP World highlight just how tricky third-party management can be. With so many partners, suppliers and subcontractors in an organization (and its subsidiaries!), managing third parties is a real puzzle for cybersecurity teams.
Once again, regulations, including DORA’s Chapter V, call for greater monitoring. To meet the regulator’s requirements, you’ll need to assess third-party risks, introduce specific clauses in contracts, and define a strategy for rapid decontractualization (stressed exit).
Efficient third-party management cannot rely on security teams alone. All departments need to be involved: IT, purchasing, business etc. A third-party evaluation platform, available to all, can engage them effectively.
You also need to involve your most critical third parties in joint crisis exercises. This kind of integrated training, still very uncommon, allows both sides to learn from each other.
Last but not least, cooperating with industry players is key to safeguarding core market assets. That’s especially true for third parties that can’t be re-insourced (e.g. large Cloud platforms), or where no alternative exists for the market (e.g. SWIFT).
Managing third parties means dealing with the risks of thousands, or even tens of thousands, of entities. It’s a major effort that calls for long-term commitment!
7. CISO: a job in the midst of change
To meet today’s challenges, CISOs (Information Systems Security Managers) are required to embrace new skills and resources.
CSOs (Chief Security Officers) are now responsible for cybersecurity, IT risks, operational resilience and sometimes even fraud – thus rationalizing controls and creating synergies. This shift often goes hand in hand with, or is preceded by, a fusion center, enabling a single point of control for all security issues (cyber, physical, fraud, etc.), in order to detect potential threats, coordinate responses and take swift decisions.
Today, a CISO’s role extends to industrial IS and product security. In the industrial sector, governance has seen significant changes in recent years. The challenge remains to change practices in the field, all the more so as there is often no “Operations” CIO, and systems are fragmented across different sites, creating a highly heterogeneous situation. In some cases, the cyber teams are even responsible for rationalizing production information for industrial sites. IT (Information Technology) and OT (Operational Technology) must merge. This means unifying IT and operational systems to improve efficiency in management and decision-making. One example is the creation of an IT/OT SOC (Security Operations Center), pooling threat detection from the IT and plant environments.
Moreover, regulatory pressure and client requirements are driving the development of product security. It is increasingly becoming a CISO concern, not just that of the business functions that historically played this role. In particular, new regulations such as the European Union’s Cyber Resilience Act and the United States’ Cyber Trust Mark require a high level of cybersecurity in all digital products, and call for a cross-functional, holistic approach. The most mature companies successfully turn these requirements into a market differentiator.
Understanding the inevitable changes in cybersecurity
8. Artificial intelligence: a double-edged tactical advantage
With all the buzz around artificial intelligence (AI), organizations are facing unprecedented threats affecting the very heart of these models. New attacks are emerging, such as poisoning (modifying training data to trick it), oracle (hijacking AIs to make them reveal things they shouldn’t), or illusion (making AIs believe things that are false but invisible to humans). New risk assessment and protection measures need to be put in place.
In the short term, the priority is therefore to secure business projects using AI, particularly in the following stages:
- Classifying AI use cases according to regulatory criteria (refer to the future European AI Act) or the NIST (National Institute of Standards and Technology) AI risk management framework.
- Defining responsibility matrix and governance for use case validation, taking into account cybersecurity, transparency, privacy, bias and ethics.
- Implementing dedicated safeguards where necessary, either by integrating security directly into the project design, or by implementing new products for AI security.
Looking ahead, you’ll have to monitor AI developments in cybersecurity. 2024 will hold plenty of interesting announcements, but we recommend not to invest prematurely. More mature companies can, however, start centralizing security data in a Security Data Hub to take advantage of AI solutions when they are mature.
The Security Data Hub
In addition to the SOC and logs, the Security Data Hub allows you to gather critical cybersecurity information in real time: protection measures operating status, patch levels deployment, threat analysis, sites and business functions criticality. Centralizing this data allows for greater automation of security operations. Some of our clients are developing this type of structure to increase event visibility, and respond to alerts more rapidly, or even automatically.
We’re still in the early days of Security Data Hubs in the field of threat detection tools; only a handful of our clients have yet embarked on building such a structure.
9. Encryption: preparing for the next generation and post-quantum
While communications and storage encryption (data at rest) has become commonplace, the encryption revolution carries on with the rise of technologies such as encryption in use. Regulators are taking an interest in these issues, as in the case of DORA. This trend calls for integration of confidential computing principles by bringing encryption right into the processor’s memory and registers. However, this can go even further, particularly with homomorphic encryption (enabling data to be processed without the need for prior decryption).
At the same time, quantum computers pose a growing threat. Although their peak impact is expected between 2030 and 2033, there are already warning signs. You need to start thinking now about which sensitive data will need to remain confidential for at least a decade.
There are three key stages in the transition to post-quantum.
- Identify sensitive data, understand its nature and strategic importance, and prioritize migration.
- Analyze thoroughly current commercial and open source encryption systems.
- Adopt post-quantum encryption solutions, even imperfect ones, for continuous testing and adjustment.
At this stage, a dual-encryption strategy, combining traditional and post-quantum methods, offers multi-layered security adapted to current and future challenges.
10. Sustainable cybersecurity: who’s in charge?
Given the urgency of the climate change situation, cybersecurity teams need to assume their share of responsibility and adopt sustainable practices that go beyond Green IT. As CISOs oversee security policies, they can also influence them to promote less energy-intensive security measures, without increasing the level of risk.
This starts with assessing the environmental impact of security measures. A number of tools allow you to measure the greenhouse gas emissions of infrastructures (both on-premises and in the cloud) and endpoints. This first step enables you to identify the most polluting devices within your organization.
The goal is then to reduce emissions without significantly compromising the level of safety, i.e. without affecting critical measures.
Initial work to provide an operational response to this issue will be published in early 2024, so stay tuned!
2024… and beyond? Preparing the future of cybersecurity
Cyber talent shortages: leveraging internal resources
Faced with a persistent shortage of talent, cybersecurity is faced with a dual challenge: recruiting, but also ensuring that current teams are happy and efficient.
Wavestone is studying clients’ cyber HR strategies. Initial results show that short-term individual fixes, such as salary increases, can be effective, but lead to significant biases. Long-term collective strategies, focusing on knowledge management and the development of communities and expertise, are not widely implemented yet yield good results. Talent retention policies, involving individual career paths and professional development, are the least implemented, even though they are the most effective in keeping talent engaged over the long term.
To meet these challenges, and in particular that of growing cybersecurity teams, we recommend developing cybersecurity’s attractiveness within your company, rather than relying on external recruitment. Encouraging internal mobility and valorizing existing skills is, according to us, the best way to balance talent needs and market realities.
New Year: some consulting tips to redefine your cyber roadmap
While all of these topics should be on your own radar, you’ll need to prioritize and orchestrate them very clearly to build a successful strategy. You’ll then need to define what you want to achieve by the end of your next strategic cycle and deploy your action plan to get there. How do you do this?
Start with a top-down approach, getting the C-Suite (Chief Information Officer, Chief Operations Officer, even Chief Executive Officer) to validate your vision. Such profiles require you to present your goals in a way that everyone can understand.
Identify the people responsible for developing and implementing your action plan. Set up a cross-functional working group, including representatives from security, production and the business lines, as well as a steering committee to assess progress, determine next steps and set performance indicators. The action plan must then be communicated to all levels of the organization to ensure widespread support.
Think about how to promote your cybersecurity strategy outside your organization. Some focus on operational efficiency, targeting high-level resilience, while others seek to highlight security as a selling point for their products or services, orienting their strategy towards trust. In all cases, formulating your ambition in one key phrase will be a must for making a lasting impression and guiding your decisions.
CISO Radar methodology
Wavestone’s CISO Radar showcases a selection of the key topics faced by cybersecurity and resilience professionals in their daily work.
It is organized into quadrants that outline core themes: Identity & Trust Services; Protect, Detect & Respond; Risk & Governance; Compliance & Privacy; and Operational Resilience.
Each of these themes is divided into three levels of maturity: “Mature,” “Trending” and “Emerging.”
- “Mature” topics can and should be mastered by any CISO.
- Topics categorized as “Trending” are beginning to be addressed operationally; initial feedback is available.
- “Emerging” subjects are still not well known or as yet have no obvious solutions. Identifying them allows you to anticipate future developments and prepare for their arrival in your organization.
