CISO Radar: what to expect in 2025?
Published January 15, 2025
- Cybersecurity

After several years of intense investment and the implementation of ambitious cyber security enhancement programs, 2025 will mark the end of a strategic cycle for many organizations. The increasingly challenging economic conditions and the desire of many management committees to rationalize spending will increase pressure on cyber budgets, with stakes remaining high.
IT systems are becoming ever more complex, perimeters less controllable, particularly with the rise of artificial intelligence, regulations are multiplying and specializing, and geopolitical tensions are increasing the overall level of cyber risk. The CISO will therefore face a major challenge: maintain, or even strengthen, security while optimizing available resources.
To prepare for this pivotal year, join us in deciphering the major trends that will transform the cybersecurity landscape in 2025 and beyond.
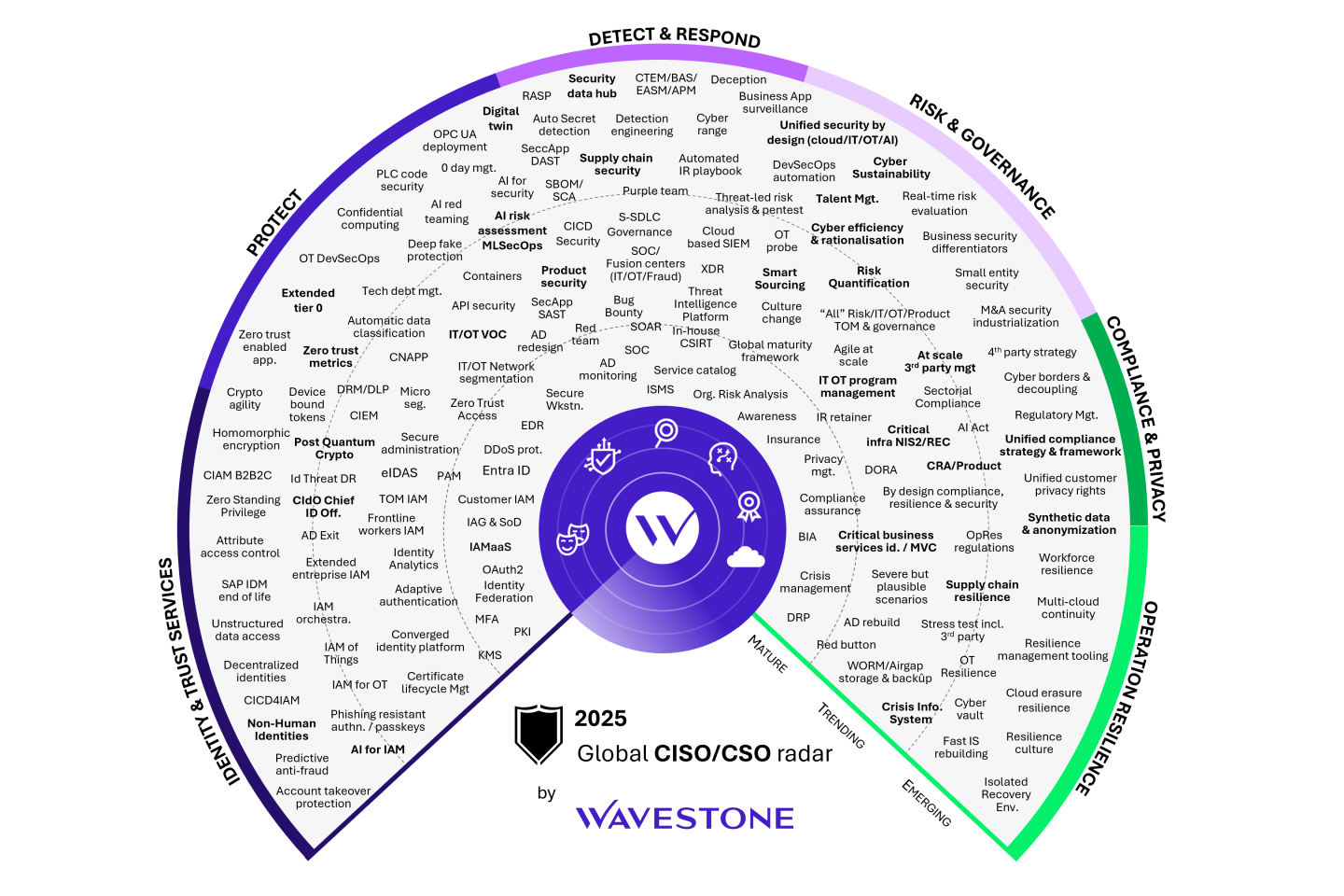
For over 10 years, Wavestone has annually updated its forecasting tool: the “CISO Radar,” which encompasses all the essential topics for cybersecurity and operational resilience sectors. Its creation is based on a collaborative effort involving all the managers and experts from our teams. This radar reflects the engagements carried out throughout the year as well as the developments observed in the field.
Based on this radar and our analyses, we have identified the three major areas that will likely shape the coming years, along with emerging topics to start keeping an eye on this year.
The need to rationalize and optimize operations
In recent years, due to the increase in cyberattacks, organizations have heavily invested in expanding and improving their cybersecurity services. Today, we are facing a slowdown of this trend, with CISOs encountering significant budgetary pressures that require rethinking their organization. However, this has not been accompanied by a reduction in threats—quite the opposite! Therefore, they must keep improving their security posture, albeit with the same resources.
1. Streamline existing processes and tools
The growth in recent years has improved the level of cybersecurity, especially in large organizations. However, the multiplication of processes and tools creates redundancies and conflicts, limiting efficiency and complicating cost control, an issue increasingly monitored by executive committees. Therefore, rationalization becomes essential.
For processes, standardizing practices between geographies or teams prevents misunderstandings, duplications, and inconsistent analyses. This approach is crucial to meet the growing needs of businesses while maintaining responsiveness. Sectors such as finance are particularly affected, especially regarding topics such as reference frameworks and control functions, which have multiplied, incident response procedures, or the integration of security into projects.
In terms of existing technologies, it may be wise to analyze your current setup to identify any overlaps. As tools are frequently updated, new features can cover areas previously managed by other dedicated solutions. Instead of multiplying distinct tools, which can be costly and complex, aim for a deliberate reduction by focusing on a few unified platforms. Some of our clients, who had between 40 and 80 cybersecurity solutions, now target around 10 tools based on 2 or 3 major platforms. Identity and Access Management (IAM) is often a priority, and infrastructure security can also benefit. Remain vigilant, however, about the gaps between vendor promises and reality, as well as the risk of dependency on a single provider, as illustrated by the CrowdStrike incident this summer.
2. Improve the management of your teams
Last year, we explored the talent shortage in the cybersecurity sector and the strategies to mitigate it. Given the current economic constraints and the increasing geographical dispersion of organizations, optimizing the placement of human resources has become essential. This approach, known as “smart sourcing,” involves identifying the right locations to find talent, balancing the need for expertise with cost efficiency:
- In your geography, to benefit from local expertise, even on-site, with high flexibility and adaptability.
- Nearshore, to optimize efforts while benefiting from geographical and linguistic proximity, and growing expertise, particularly in Portugal or Eastern Europe for European-based organizations, Mexico or South America for North America, or Southeast Asia for Pacific Asia.
- Offshore, to reduce costs on already mature processes, while remaining attentive to final efficiency. The most common destination countries remain India and Southeast Asia.
In parallel, in an always very tight cybersecurity job market, it is essential to keep internal teams aligned with your organization’s long-term vision. To achieve this, a “Talent Management” approach must be implemented to properly manage a truly key sector within the organization. Without going over all the best practices, some major points must be considered:
- Create a team spirit with common practices and rituals, especially to share expertise and skills.
- Promote team development by offering training opportunities and clear, long-term career plans.
- Value your experts and stay attentive to their aspirations.
To find the right balance, analyze your existing processes, their maturity, their importance for the security of your assets, and the desired geographical coverage. “Smart sourcing” can be very beneficial by freeing up time for hands-on or management tasks. However, you can only effectively outsource what you master, and massive offshoring can lead to negative effects on several levels. Once again, this becomes a risk management task for the CISO, but this time from an HR perspective!
3. Be able to demonstrate the value of cybersecurity
In a context of limited resources, it becomes essential to prove the value of cybersecurity. Two actions can be taken:
It allows for a concrete evaluation of the impact of security measures on financial, operational, and strategic levels. Thanks to emerging solutions, this exercise is more accessible and facilitates communication with executive committees, allowing for the prioritization of actions. This approach works in all sectors.
Cybersecurity is increasingly crucial for earning the trust of customers and partners and securing market opportunities and can even generate new offers. CISOs must therefore master the business, understand customer journeys, and collaborate with business teams. In the long run, cybersecurity can transition from a cost center to a profit center, often requiring the mobility of business profiles to bring a marketing and commercial dimension. This approach is very effective in contexts where the organization builds and markets digital offerings or products (industry, healthcare, automotive, transport, etc.).
While ensuring the scaling of key cyber challenges!
Traditionally, organizations have prioritized strengthening the security of the core of their IT systems, and according to field feedback, they have generally succeeded. But cyber attackers have adapted their tactics: they now target small entities and subsidiaries, privileged accounts, or cloud vulnerabilities to access less defended areas. Regulators, for their part, require increased attention to suppliers and the securing of expanded perimeters.
All this, in a tense geopolitical context where standardizing practices is no longer always possible with the increase in compartmentalization, to anticipate or meet decoupling needs for regulatory or geopolitical reasons. We had already noted this trend in our previous radar edition, and it remains relevant today.
Scaling up is essential but remains complex and seems to approach the impossible! Informed, reasoned choices must be made, in line with the IT department’s and organization’s strategy, and debated at the right level. Of course, three important activities must continue in 2025:
- Maximizing the potential of the Cloud. While it offers benefits for IT as well as cybersecurity, as we discussed last year, this new infrastructure—and particularly its administration—must be secured. Leverage Microsoft’s Enterprise Access Model to adapt the concept of tiering to your cloud environments and integrate massive cloud unavailability scenarios into your crisis exercises and resilience plans.
- Developing CI/CD pipelines: beneficial due to the automation and standardization of practices for better integrating security into projects. It is becoming a systemic component of the IT system and can, if poorly protected, lead to its complete compromise! Ensure this transformation does not backfire by treating it as almost as critical as a “new Active Directory.”
- And, of course, Zero Trust, a crucial initiative we identified last year. Governance will be key for this deep transformation: designate a leader and ensure that all relevant stakeholders are gathered at the table (network, infrastructure, developers and architects, and business teams).
For 2025, we have also identified five key areas to ensure control over this ever evolving and complex scope, as well as the infrastructures supporting it.
Last year, we emphasized the importance of third-party management, a long-term effort. This observation remains more relevant than ever, but your subsidiaries and small entities also represent a risk, especially when they join your organization through a merger or acquisition. Boundaries are blurring: entities are less monolithic and maintain multiple, sometimes vastly different, connections, where visibility on security posture and action capability is limited.
Ensure security governance is adapted to these new configurations:
- On the organizational level, ensure that your requirements and frameworks effectively cover all entities and third parties. The ability to control the application of your policies will be crucial: simplified analysis tools can help you (e.g., to evaluate your suppliers’ responses). Also, make sure that all relevant teams (legal, procurement, business, local security) are included. Some large organizations have hundreds of more or less autonomous subsidiaries and thousands, or even tens of thousands, of suppliers.
- In terms of responsibilities, the role of the “CISO,” a catch-all for years, is still set to expand: operational resilience, fraud, IT risk management, product security… Due to the growing importance of identity, the role of “Chief Identity Officer” (CIdO) is emerging to manage and protect both internal and external IAM, and even that of objects or non-human identities. In the industry, “OT Security Officers” focus on industrial systems, and “Product Security Officers” on the security of digital products. In this context of rationalization and specialization, adopting clear governance will be necessary to communicate the allocation of responsibilities to all concerned parties and to mobilize the entire organization. Never forget that the stronger the delegation, the more the culture will have changed, and the more deeply secured the organization will be!
As many organizations reach a period of renewal for their Security Operation Center (SOC), it is essential to maintain or even enhance its effectiveness, despite an ever-expanding and increasingly heterogeneous scope. Several key areas of focus are emerging:
- Optimizing the SOC: automation (via traditional SOAR tools or new AI-powered products) promises to accelerate processes and facilitate analysts’ work. While the results are promising, achieving this requires significant foundational efforts. “Shift-left” as well as specialized decentralized tools (as opposed to legacy centralized monolithic SIEM) and teams are seen as levers enabling to scale up and structurally optimize the SOC.
- Rethinking the technology stack: numerous SOC overhaul projects are currently in the planning phase. These projects often lead to strategic decisions: discontinuing SIEM? Focusing on XDR? Migrating to the cloud? Implementing “detection as code” to streamline the automated addition and removal of detection rules? Depending on the needs (IT/OT/Product coverage, technological diversity) and existing tools (end-of-life products, acquired solutions, etc.), the directions being taken by clients vary significantly based on priorities such as managing heterogeneous environments and simplifying operations.
- Revisiting data management for real-time capabilities: beyond the usual collection of “cold” logs, creating a Security Data Hub can unify security events and consolidate relevant data sources, providing a more real-time view of the security posture. This transformative approach requires advanced “data” thinking to structure the data hub, but it offers short-term benefits in understanding exposure levels continuously and long-term advantages, particularly for integrating AI.
When the most advanced organizations master these three pillars, they will then be able to move toward Continuous Threat Exposure Management. Combining multiple tools and methodologies (Attack Path Management, Extended Attack Surface Management, Breach & Attack Simulation), this approach enables organizations to prioritize their detection and remediation efforts based on the most probable and critical intrusion scenarios, relevant to their specific context.
Data protection is a major challenge for organizations, as they manage a multitude of critical data necessary for their proper functioning. Knowing how to monitor the security level of this data has long been a thorny issue. Solutions have emerged over the years to address this challenge (data encryption, auto-discovery, real-time anomaly detection, etc.), but none have provided a perfect answer.
Today, thanks to artificial intelligence, new tools seem to be emerging to offer an effective solution. 2025 could be an opportunity for CISOs to seize the new opportunities offered by AI to enhance the functionalities of the two main categories of tools:
- DSP (Data Security Platforms) aim to provide comprehensive data protection, including threat detection, access management, and regulatory compliance. They are gradually integrating AI features to enhance their services.
- DSPM (Data Security Posture Management) could also benefit from the integration of AI. Various types of DSPM exist, each addressing specific needs, particularly regarding adaptation to Cloud environments. These tools centralize data security management, offering an overview and tools to monitor and strengthen data security management. The addition of AI could facilitate the correlation between different data sets, suggest appropriate posture adjustments, and maintain continuous risk analysis and trend monitoring, especially through improved auto-discovery tools.
To ensure you have the most suitable tools for your needs, take advantage of the new year to:
- Ensure that the data owners within your organization are clearly identified.
- Analyze how you currently secure your data.
- Identify the challenges you face and the features you would like to have to address them.
- Define the environments in which your information system is present and interacts, and the resources that are and will be allocated for data security management.
- Keep a close watch on existing solutions and choose those that best meet your needs.
The scope is expanding…, and so is the volume of vulnerabilities! Many organizations are dealing with growing backlogs of unaddressed vulnerabilities affecting all components, including operating systems, middleware, applications, and network equipment. Recent cyber incidents highlight that exploiting these vulnerabilities is a favored tactic for attackers. To scale and industrialize our response, adopting a Vulnerability Operation Center (VOC) approach is essential.
The two objectives of the VOC are to enable automation and efficiency gains. The VOC acts as an orchestrator for vulnerability management by combining:
- Governance with a clear organization of tasks and responsibilities (regarding which vulnerabilities to remediate, which areas to monitor, etc.).
- A platform that centralizes vulnerabilities detected by all types of tools (SAST, DAST, IAT) to streamline and prioritize remediation.
The VOC is the art of harmonizing: we set up a conductor to control vulnerability management by reconciling a wide variety of sources and bringing together multiple teams. The deployment of this type of structure for many clients shows positive results, allowing for clearer responsibilities and significantly reducing critical vulnerabilities.
2024 has shown that AI is becoming an increasingly essential tool for businesses, and it seems unrealistic to do without it. Therefore, it is crucial to secure it.
For now, most of the use cases we have observed are fairly straightforward, even if some are critical, and organizations have been quick to grasp them by deploying, at the very least, appropriate governance and basic security measures. However, with the rise of “agentic” AI, capable of executing tasks or making decisions, the risks will increase and diversify. It will then be necessary to adopt more complex and AI-specific approaches, with a precise understanding of your profile:
- Are you simply a user of AI systems provided by third parties? In this case, focus on managing and assessing the risks associated with these third-party AI model/system providers, as well as on raising awareness and controlling your users.
- Do you develop applications that integrate AI models provided by third parties? You must then secure the platform hosting the AI, ensure data protection, and perform checks on the entire solution.
- Are you yourself a creator and operator of AI models (or even a provider for others)? Integrate security throughout the development cycle and plan for extensive testing (AI red teaming). Ensure you can detect and respond to incidents, particularly in the face of potential malicious prompts for generative AI.
These essential steps for cybersecurity are part of the broader approach to trustworthy AI, focusing on lawful, ethical, and robust AI systems aligned with frameworks like the NIST AI Risk Management Framework or the European AI Act. This involves governance that fosters dialogue among all organizational stakeholders (cybersecurity, data science, legal, business, etc.), tailored processes, appropriate tools (charters, risk assessment methodologies, etc.), and controls (audits, red teaming, etc.).
Make the most of the compliance boom with “regulatory management”
Different regions of the world are experiencing a wave of regulations affecting many subjects and sectors. In the United States, there is the CMMC 2.0 directive or FED/FEB; in Europe, the Cyber Resilience Act, NIS2, AI Act, DORA, REC… Other sectoral frameworks (Part-IS in aviation, UNR 155 for connected vehicles, and so on…) add to this long list. Historically focused on the protection of personal data or critical infrastructures, these regulations have expanded to more themes, sectors, and organizations. Now, almost no sector or company size is spared, and the influence of regulators continues to grow.
Even if these regulatory constraints may seem distant from business priorities, properly addressing them can be beneficial: clarifying processes, launching major projects, and highlighting your efforts to management.
Cyber regulation management will therefore be a key issue in 2025:
- If not already done, establish an organization to identify and monitor the regulations that apply (or will apply) to you. Integrate them into your cyber roadmaps. Linked to the CISO and in close collaboration with legal or compliance teams, this entity should have a regulatory dashboard, including a mapping of texts and their application scopes (for NIS2 alone, the analysis must be carried out in the European subsidiaries of the 27 countries). Also, define Group rules to avoid inconsistent and costly implementations. Some clients even unify their security policy at the Group level to respond to most texts with a single framework.
- For the most mature organizations with adequate resources, move to “regulatory management.” Take inspiration from the US financial sector: its most advanced players have set up active monitoring and dedicated teams that regularly interact with regulators, contribute to guidelines, and stay informed of new requirements in advance. They also organize regulator visits and the preparation and follow-up of audits, a crucial step in some sectors (such as finance), where audits can be long and demanding and disrupt regular activities.
What are the future challenges?
Beyond the underlying trends, a number of issues will begin to take center stage in 2025, requiring each cybersecurity sector to position itself on their relevance in their context.
To bypass the massive protections deployed on infrastructures, cyber attackers are increasingly targeting Identity and Access Management (IAM) systems. These systems can present the same vulnerabilities as other security components (token theft through man-in-the-middle attacks, application flaws…), making authentication bypassable or exploitable. To protect yourself:
- Conduct a security audit specifically focused on IAM to check your platforms and account assignment processes (disabling strong authentication, resetting passwords, lost phones…).
- Review the security of administrative accounts, including those dedicated to IAM, to prevent a compromise from allowing privilege escalation (e.g., a support account that can reset the password and MFA of a domain administrator).
- Secure the connection between the IAM system and your applications to ensure that only authorized individuals access the required resources and be vigilant against application masking that facilitates lateral movements.
Even the most advanced players have already suffered this type of attack: make it a key element of your 2025 control plan!
Increased awareness and new regulations (e.g. Cyber Resilience Act) are making consumers of digital products (both professional and personal) more demanding regarding their security. Some of our clients have already understood this.
The main challenge lies in bringing together dispersed expertise (product managers, developers, business units, marketing, support, compliance, etc.). It involves identifying your digital products and creating an integrated sector to consolidate skills and simplify security integration. Some organizations have established a Product Security Office, usually attached to the CISO, which ensures regulatory compliance and a minimum level of security. In the long run, this setup can demonstrate the value of cybersecurity and make it a differentiating factor. To get started:
- Assess the security of your digital products (including software solutions) and the measures in place, comparing them with regulations and customer expectations.
- Identify stakeholders in the product lifecycle, their current roles, and actions to be strengthened. Assign them a security point of contact.
- Establish dedicated governance, initially in the form of a task force, then evolve it into an integrated approach with specific processes, especially for regulatory compliance.
Cyber sectors have already addressed AI security, although much remains to be done in an ever-evolving context. After this initial phase, it is time in 2025 to see how the CISO can leverage AI to enhance their own activities. Today, the market is still being structured, but some use cases are beginning to reach maturity. We can identify:
- Facilitating communication (awareness campaigns, access to security documentation, “CISO GPT” to answer complex questions).
- Accelerating certain processes (pre-analysis of your suppliers’ responses to security questionnaires).
Other, more distant use cases also deserve your attention:
- Data protection: recommending classification levels based on nature and context, for instance.
- Detection & response: AI assistants for the SOC, automated log searches, dynamic updating of detection rules.
The priority, however, is on combating the rise of deepfakes (particularly their use in CEO fraud). AI will likely be key to achieving the necessary responsiveness, and innovative solutions are already beginning to emerge.
For now, maintain close monitoring and evaluate the productivity and efficiency gains that AI can bring you. In a context where resource optimization is crucial, AI could prove to be a valuable ally. Many AI-based products are expected to appear in 2025: identify relevant use cases now to stay proactive and effective.
A key topic in IT security, cyber resilience is also crucial for the OT world. The Critical Entities Resilience Directive in Europe will soon require industrial players to integrate this topic into their roadmap. Fortunately, resilience is already well-known in the industry, with existing processes often adaptable to cyber: redundancy, incident communication, business continuity plans, and local degraded processes.
However, this analysis is often done at the scale of a site or a production line, without an end-to-end vision. The worst-case scenario considered is local and not a global industrial IT failure following a cyber attack.
Moreover, industrial IT architectures, although segmented, often lack isolation, detection, and, most importantly, rapid reconstruction capabilities! To address these scenarios, response formats and modes need to be adapted: dedicated and isolated crisis management PCs, adjusted reflex sheets, and recovery tests that include this end-to-end vision.
The industrial world is well-acquainted with resilience, and IT departments have been working on it for a long time: fully bring these two worlds together to make your OT infrastructure completely resilient!
Most estimates suggest that a quantum computer capable of breaking RSA encryption will emerge between 2030 and 2040. Authorities and standardization bodies have already acted: NIST published the first post-quantum encryption standards this summer, and at the end of November 18 European security agencies recommended making it a major priority. In Australia, obsolescence dates for RSA and ECC as we know them have even been set for 2030.
Why such a hurry?
- We must prepare for a long migration, covering a wide scope (infrastructure, suppliers, products…), which can span several years.
- For certain sensitive areas, malicious actors could “harvest now and decrypt later” when quantum computers become operational.
As of 2025, anticipate:
- Raise awareness among business units and executive committees, as this project remains largely invisible outside IT teams but will require financial support.
- Define your strategy by identifying the data to be protected as a priority (especially those with long confidentiality periods or highly exposed). Conduct a quick inventory of your trust systems (PKI, HSM, CLM…) to assess the migration effort and meet future regulatory requirements.
- Clarify governance (cyber team? IT team?) and appoint a strong leader to oversee the project over several years.
- Integrate post-quantum compliance requirements (PQC) into your cyber clauses, either now or through updates within three years. For those most affected, launch POCs.
- Add this transition to your obsolescence roadmaps to benefit from existing processes.
- Embed all these actions in a “crypto agility” logic, as post-quantum algorithms are still young and may require several future migrations.
Disinformation is a major societal issue that large organizations are subjected to and sometimes find themselves powerless against. Without replacing communication teams or ensuring continuous monitoring of social networks, the CISO can nevertheless contribute in the case of a confirmed disinformation campaign: analysis methodologies, investigations, processing data from incident response… Their technical expertise can thus enhance the organization’s credibility and showcase the teams’ know-how. Beyond combating fraud, managing disinformation could therefore become an additional skill for the CISO, especially in the most mature and exposed areas.
Methodology of the CISO Radar
The CISO Radar presents a selection of key topics for cybersecurity and resilience professionals, which they are required to handle in their activities.
It is organized into quadrants that outline core themes: Identity & Trust Services; Protect, Detect & Respond; Risk & Governance; Compliance & Privacy; and Operational Resilience.
Each of these themes is divided into three maturity levels: “Mature,” “Current,” and “Emerging”.
- Themes at the “Mature” level can and should be mastered by any CISO.
- Topics categorized as “Trending” are beginning to be addressed operationally; initial feedback can be shared.
- In the “Emerging” level, you will find topics that are still relatively unknown, evolving, or for which there are no obvious solutions. Identifying them allows you to anticipate future developments and prepare for their integration into your organization.
The identification of themes, their positioning, and their analyses result from a joint effort conducted by the Cybersecurity Practice management teams at Wavestone across all the firm’s geographies.